
Quantum Computing: Revolutionizing Tech & Security
Quantum Computing: Revolutionizing Tech & Security
Quantum Computing: Revolutionizing Tech & Security
Introduction
Introduction
Introduction
The quantum revolution is here. With the unveiling of Willow, Google's quantum computing chip, the world is witnessing a breakthrough in solving problems once thought insurmountable. In benchmark tests, Willow completed a computation in under five minutes — a task that would take the world’s most powerful supercomputer over 10^25 years. This leap in quantum computing capabilities promises to transform industries and challenge everything from AI to cryptography.
In this blog, we will explore how quantum computing works, its profound implications for cryptography, and why it's a game-changer for the future of digital security and technology.
The quantum revolution is here. With the unveiling of Willow, Google's quantum computing chip, the world is witnessing a breakthrough in solving problems once thought insurmountable. In benchmark tests, Willow completed a computation in under five minutes — a task that would take the world’s most powerful supercomputer over 10^25 years. This leap in quantum computing capabilities promises to transform industries and challenge everything from AI to cryptography.
In this blog, we will explore how quantum computing works, its profound implications for cryptography, and why it's a game-changer for the future of digital security and technology.
The quantum revolution is here. With the unveiling of Willow, Google's quantum computing chip, the world is witnessing a breakthrough in solving problems once thought insurmountable. In benchmark tests, Willow completed a computation in under five minutes — a task that would take the world’s most powerful supercomputer over 10^25 years. This leap in quantum computing capabilities promises to transform industries and challenge everything from AI to cryptography.
In this blog, we will explore how quantum computing works, its profound implications for cryptography, and why it's a game-changer for the future of digital security and technology.
Quick Summary
Quick Summary
Quick Summary
Quantum Computers use qubits to perform complex computations exponentially faster than classical computers.
Quantum Supremacy has been demonstrated by Google's Willow chip, revolutionizing traditional computation methods.
Cryptography faces an existential threat from quantum algorithms, necessitating the development of Post-Quantum Cryptography (PQC) solutions.
PQC Solutions like lattice-based cryptography are key to ensuring the security of data in the quantum future.
Geopolitical Impacts: Quantum computing will influence global competition, privacy, and security.
Quantum Computers use qubits to perform complex computations exponentially faster than classical computers.
Quantum Supremacy has been demonstrated by Google's Willow chip, revolutionizing traditional computation methods.
Cryptography faces an existential threat from quantum algorithms, necessitating the development of Post-Quantum Cryptography (PQC) solutions.
PQC Solutions like lattice-based cryptography are key to ensuring the security of data in the quantum future.
Geopolitical Impacts: Quantum computing will influence global competition, privacy, and security.
Quantum Computers use qubits to perform complex computations exponentially faster than classical computers.
Quantum Supremacy has been demonstrated by Google's Willow chip, revolutionizing traditional computation methods.
Cryptography faces an existential threat from quantum algorithms, necessitating the development of Post-Quantum Cryptography (PQC) solutions.
PQC Solutions like lattice-based cryptography are key to ensuring the security of data in the quantum future.
Geopolitical Impacts: Quantum computing will influence global competition, privacy, and security.
Understanding Quantum Computing
At its core, quantum computers leverage the strange fundamental properties of subatomic particles, such as entanglement and superpositio,n with the ability to perform computations far beyond the realm of classical computers. While classical computers use bits (0s and 1s), quantum computers use qubits, which can exist in multiple states simultaneously. This unique property allows quantum computers to solve certain types of problems exponentially faster than classical computers.
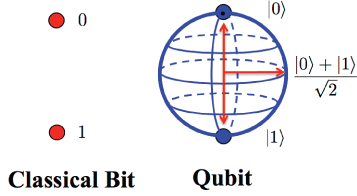
Fig 1: Bits vs Qubits
Why Quantum Computing is a Game-Changer for Cryptography
Quantum computing is set to revolutionize a range of fields, including artificial intelligence, supply chain optimization, complex molecular simulations for drug discovery, and climate modeling. Beyond these practical applications, quantum computing is envisioned as a tool for understanding the true nature of reality, as it can simulate the behavior of fundamental particles with high accuracy.
But perhaps their most profound and alarming impact lies in cryptography and security. The digital world relies heavily on cryptographic systems such as RSA and ECC to secure communication channels, safeguard sensitive data, and protect financial systems. These encryption standards leverage the fact that factoring very large numbers is resource-heavy and time-consuming for classical computers.
However, these systems are not designed to withstand the capabilities of quantum algorithms like Shor’s, leaving them vulnerable in a post-quantum world. Shor’s algorithm can efficiently solve problems such as integer factorization and discrete logarithms. This threatens the security of widely used protocols such as RSA and ECC, posing a serious threat to encryption.
While symmetric encryption schemes like AES (Advanced Encryption Standard) are less vulnerable to quantum attacks, Grover’s algorithm (another quantum algorithm) reduces the effective key length by half, necessitating longer keys to maintain security, hence requiring more computing power.
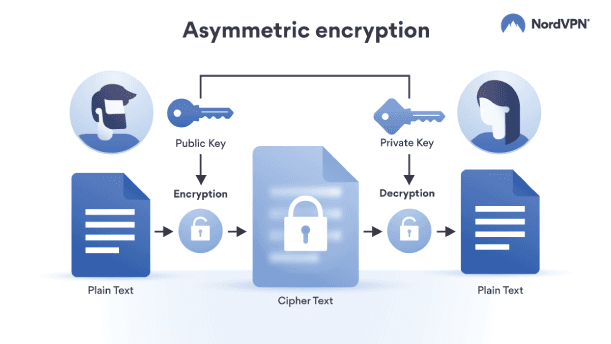
Fig 2: Modern-day encryption
Preparing for the Post-Quantum World: What Are PQC Solutions?
To address the looming threat posed by these new computers, researchers around the world are developing post-quantum cryptographic protocols that rely on problems believed to be hard for both classical and quantum computers. These include lattice-based, hash-based, code-based, and isogeny-based algorithms.
Among these, lattice-based cryptography is one of the most promising approaches due to its efficiency and strong security guarantees. Most researchers also advocate for interim standard solutions that combine classic and post quantum cryptography(PQC) standards during transition.
Organizations like NIST are working to standardize quantum-safe algorithms to replace RSA and ECC in the coming decades. Notable examples include CRYSTALS-Kyber for key exchange and CRYSTALS-Dilithium for digital signatures.
Lattice-Based Cryptography: Known for its efficiency and security.
Hash-Based Cryptography: Another strong contender with potential applications in digital signatures.
Code-Based Cryptography: Secure, with long-standing research backing its viability.
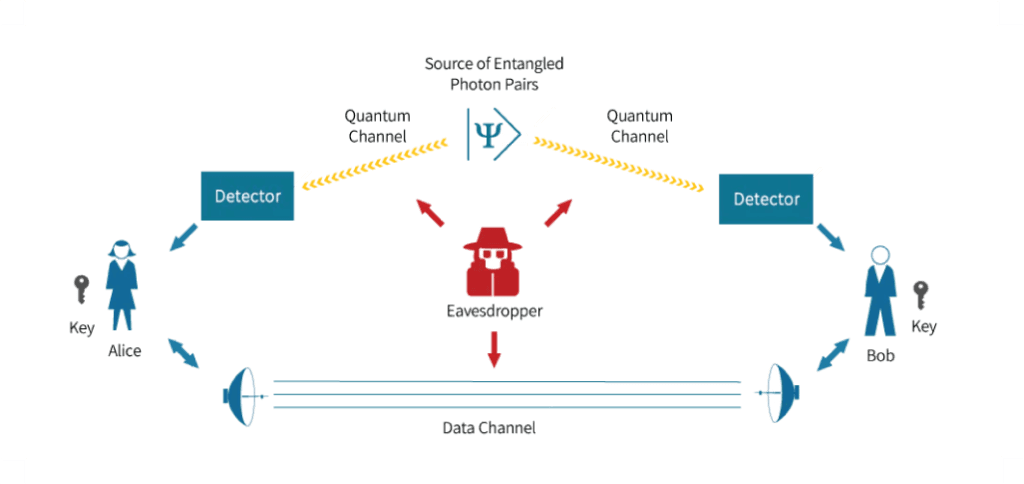
Fig 3: Quantum Encryption
Quantum Computing and Geopolitical Impacts
As quantum computers advance, the threat of “harvest-now, decrypt-later” attacks looms larger. These attacks involve adversaries capturing encrypted data today, with the aim of decrypting it in the future when quantum computers gain the capability to break current cryptographic protocols.
Encrypted data intercepted today could be stored and decrypted later, making immediate adoption of PQC a necessity for long-term security.
Beyond cryptography, the rise of quantum computing will influence geopolitics, economics, and innovation. Governments and industries must consider not only the technological implications but also the ethical challenges of deploying systems that could redefine privacy and security.
The rise of quantum machines would be a technological landmark, taking humanity to new heights of innovation. While it poses a considerable threat to traditional cryptographic systems, it also offers the chance to innovate and strengthen digital security through post-quantum cryptography.
By acting now, we can safeguard the future of our digital world against the inevitable quantum revolution.
Closing Thoughts
The emergence of quantum computing is poised to reshape industries, particularly in fields like AI, drug discovery, and cryptography. While it poses a major threat to current encryption standards, it also presents the opportunity to build more secure, quantum-resistant systems through post-quantum cryptography.
By taking proactive steps, organizations can safeguard their data against the inevitable quantum revolution.
Looking to secure your data for the quantum future?
Contact Cygnus Consulting today to explore quantum-safe solutions for your business.
Understanding Quantum Computing
At its core, quantum computers leverage the strange fundamental properties of subatomic particles, such as entanglement and superpositio,n with the ability to perform computations far beyond the realm of classical computers. While classical computers use bits (0s and 1s), quantum computers use qubits, which can exist in multiple states simultaneously. This unique property allows quantum computers to solve certain types of problems exponentially faster than classical computers.

Fig 1: Bits vs Qubits
Why Quantum Computing is a Game-Changer for Cryptography
Quantum computing is set to revolutionize a range of fields, including artificial intelligence, supply chain optimization, complex molecular simulations for drug discovery, and climate modeling. Beyond these practical applications, quantum computing is envisioned as a tool for understanding the true nature of reality, as it can simulate the behavior of fundamental particles with high accuracy.
But perhaps their most profound and alarming impact lies in cryptography and security. The digital world relies heavily on cryptographic systems such as RSA and ECC to secure communication channels, safeguard sensitive data, and protect financial systems. These encryption standards leverage the fact that factoring very large numbers is resource-heavy and time-consuming for classical computers.
However, these systems are not designed to withstand the capabilities of quantum algorithms like Shor’s, leaving them vulnerable in a post-quantum world. Shor’s algorithm can efficiently solve problems such as integer factorization and discrete logarithms. This threatens the security of widely used protocols such as RSA and ECC, posing a serious threat to encryption.
While symmetric encryption schemes like AES (Advanced Encryption Standard) are less vulnerable to quantum attacks, Grover’s algorithm (another quantum algorithm) reduces the effective key length by half, necessitating longer keys to maintain security, hence requiring more computing power.

Fig 2: Modern-day encryption
Preparing for the Post-Quantum World: What Are PQC Solutions?
To address the looming threat posed by these new computers, researchers around the world are developing post-quantum cryptographic protocols that rely on problems believed to be hard for both classical and quantum computers. These include lattice-based, hash-based, code-based, and isogeny-based algorithms.
Among these, lattice-based cryptography is one of the most promising approaches due to its efficiency and strong security guarantees. Most researchers also advocate for interim standard solutions that combine classic and post quantum cryptography(PQC) standards during transition.
Organizations like NIST are working to standardize quantum-safe algorithms to replace RSA and ECC in the coming decades. Notable examples include CRYSTALS-Kyber for key exchange and CRYSTALS-Dilithium for digital signatures.
Lattice-Based Cryptography: Known for its efficiency and security.
Hash-Based Cryptography: Another strong contender with potential applications in digital signatures.
Code-Based Cryptography: Secure, with long-standing research backing its viability.

Fig 3: Quantum Encryption
Quantum Computing and Geopolitical Impacts
As quantum computers advance, the threat of “harvest-now, decrypt-later” attacks looms larger. These attacks involve adversaries capturing encrypted data today, with the aim of decrypting it in the future when quantum computers gain the capability to break current cryptographic protocols.
Encrypted data intercepted today could be stored and decrypted later, making immediate adoption of PQC a necessity for long-term security.
Beyond cryptography, the rise of quantum computing will influence geopolitics, economics, and innovation. Governments and industries must consider not only the technological implications but also the ethical challenges of deploying systems that could redefine privacy and security.
The rise of quantum machines would be a technological landmark, taking humanity to new heights of innovation. While it poses a considerable threat to traditional cryptographic systems, it also offers the chance to innovate and strengthen digital security through post-quantum cryptography.
By acting now, we can safeguard the future of our digital world against the inevitable quantum revolution.
Closing Thoughts
The emergence of quantum computing is poised to reshape industries, particularly in fields like AI, drug discovery, and cryptography. While it poses a major threat to current encryption standards, it also presents the opportunity to build more secure, quantum-resistant systems through post-quantum cryptography.
By taking proactive steps, organizations can safeguard their data against the inevitable quantum revolution.
Looking to secure your data for the quantum future?
Contact Cygnus Consulting today to explore quantum-safe solutions for your business.
Understanding Quantum Computing
At its core, quantum computers leverage the strange fundamental properties of subatomic particles, such as entanglement and superpositio,n with the ability to perform computations far beyond the realm of classical computers. While classical computers use bits (0s and 1s), quantum computers use qubits, which can exist in multiple states simultaneously. This unique property allows quantum computers to solve certain types of problems exponentially faster than classical computers.

Fig 1: Bits vs Qubits
Why Quantum Computing is a Game-Changer for Cryptography
Quantum computing is set to revolutionize a range of fields, including artificial intelligence, supply chain optimization, complex molecular simulations for drug discovery, and climate modeling. Beyond these practical applications, quantum computing is envisioned as a tool for understanding the true nature of reality, as it can simulate the behavior of fundamental particles with high accuracy.
But perhaps their most profound and alarming impact lies in cryptography and security. The digital world relies heavily on cryptographic systems such as RSA and ECC to secure communication channels, safeguard sensitive data, and protect financial systems. These encryption standards leverage the fact that factoring very large numbers is resource-heavy and time-consuming for classical computers.
However, these systems are not designed to withstand the capabilities of quantum algorithms like Shor’s, leaving them vulnerable in a post-quantum world. Shor’s algorithm can efficiently solve problems such as integer factorization and discrete logarithms. This threatens the security of widely used protocols such as RSA and ECC, posing a serious threat to encryption.
While symmetric encryption schemes like AES (Advanced Encryption Standard) are less vulnerable to quantum attacks, Grover’s algorithm (another quantum algorithm) reduces the effective key length by half, necessitating longer keys to maintain security, hence requiring more computing power.

Fig 2: Modern-day encryption
Preparing for the Post-Quantum World: What Are PQC Solutions?
To address the looming threat posed by these new computers, researchers around the world are developing post-quantum cryptographic protocols that rely on problems believed to be hard for both classical and quantum computers. These include lattice-based, hash-based, code-based, and isogeny-based algorithms.
Among these, lattice-based cryptography is one of the most promising approaches due to its efficiency and strong security guarantees. Most researchers also advocate for interim standard solutions that combine classic and post quantum cryptography(PQC) standards during transition.
Organizations like NIST are working to standardize quantum-safe algorithms to replace RSA and ECC in the coming decades. Notable examples include CRYSTALS-Kyber for key exchange and CRYSTALS-Dilithium for digital signatures.
Lattice-Based Cryptography: Known for its efficiency and security.
Hash-Based Cryptography: Another strong contender with potential applications in digital signatures.
Code-Based Cryptography: Secure, with long-standing research backing its viability.

Fig 3: Quantum Encryption
Quantum Computing and Geopolitical Impacts
As quantum computers advance, the threat of “harvest-now, decrypt-later” attacks looms larger. These attacks involve adversaries capturing encrypted data today, with the aim of decrypting it in the future when quantum computers gain the capability to break current cryptographic protocols.
Encrypted data intercepted today could be stored and decrypted later, making immediate adoption of PQC a necessity for long-term security.
Beyond cryptography, the rise of quantum computing will influence geopolitics, economics, and innovation. Governments and industries must consider not only the technological implications but also the ethical challenges of deploying systems that could redefine privacy and security.
The rise of quantum machines would be a technological landmark, taking humanity to new heights of innovation. While it poses a considerable threat to traditional cryptographic systems, it also offers the chance to innovate and strengthen digital security through post-quantum cryptography.
By acting now, we can safeguard the future of our digital world against the inevitable quantum revolution.
Closing Thoughts
The emergence of quantum computing is poised to reshape industries, particularly in fields like AI, drug discovery, and cryptography. While it poses a major threat to current encryption standards, it also presents the opportunity to build more secure, quantum-resistant systems through post-quantum cryptography.
By taking proactive steps, organizations can safeguard their data against the inevitable quantum revolution.
Looking to secure your data for the quantum future?
Contact Cygnus Consulting today to explore quantum-safe solutions for your business.
Frequently Asked Questions
Frequently Asked Questions
What is quantum computing?
Quantum computing is a field of computing that uses the principles of quantum mechanics—including superposition and entanglement—to solve complex problems far beyond the reach of classical computers.
What is quantum computing?
Quantum computing is a field of computing that uses the principles of quantum mechanics—including superposition and entanglement—to solve complex problems far beyond the reach of classical computers.
What is quantum computing?
Quantum computing is a field of computing that uses the principles of quantum mechanics—including superposition and entanglement—to solve complex problems far beyond the reach of classical computers.
How does quantum computing differ from classical computing?
Unlike classical computers, which use bits (0 or 1), quantum computers use qubits that can represent multiple states simultaneously, enabling them to process many possibilities simultaneously.
How does quantum computing differ from classical computing?
Unlike classical computers, which use bits (0 or 1), quantum computers use qubits that can represent multiple states simultaneously, enabling them to process many possibilities simultaneously.
How does quantum computing differ from classical computing?
Unlike classical computers, which use bits (0 or 1), quantum computers use qubits that can represent multiple states simultaneously, enabling them to process many possibilities simultaneously.
Will quantum computers replace classical computers?
No,quantum computers are expected to complement classical systems by handling specific complex tasks, while classical computers will continue powering everyday computing.
Will quantum computers replace classical computers?
No,quantum computers are expected to complement classical systems by handling specific complex tasks, while classical computers will continue powering everyday computing.
Will quantum computers replace classical computers?
No,quantum computers are expected to complement classical systems by handling specific complex tasks, while classical computers will continue powering everyday computing.
Are quantum computers a threat to current encryption methods?
Yes,large‑scale quantum computers could break widely used cryptographic systems like RSA and ECC, creating a need for quantum‑resistant security.
Are quantum computers a threat to current encryption methods?
Yes,large‑scale quantum computers could break widely used cryptographic systems like RSA and ECC, creating a need for quantum‑resistant security.
Are quantum computers a threat to current encryption methods?
Yes,large‑scale quantum computers could break widely used cryptographic systems like RSA and ECC, creating a need for quantum‑resistant security.
What is post‑quantum cryptography (PQC)?
Post‑quantum cryptography includes encryption algorithms designed to be secure against attacks from quantum computers, helping protect data as quantum technology advances.
What is post‑quantum cryptography (PQC)?
Post‑quantum cryptography includes encryption algorithms designed to be secure against attacks from quantum computers, helping protect data as quantum technology advances.
What is post‑quantum cryptography (PQC)?
Post‑quantum cryptography includes encryption algorithms designed to be secure against attacks from quantum computers, helping protect data as quantum technology advances.